Implementing controlled-access security is essential for secure remote work environments. Biometric scanners and monitored entry systems reduce unauthorized access by up to 50%. VPNs, cloud collaboration tools, and cybersecurity training protect data and enhance productivity among distributed teams. Regular policy audits and backups further safeguard sensitive information. These measures enable seamless remote collaboration, driving innovation despite physical distances.
In today’s rapidly evolving work environment, remote-work infrastructure has become a cornerstone for organizational agility and productivity. As more companies embrace distributed teams, establishing robust and secure controlled-access security systems is no longer an option but a necessity. The current landscape demands innovative solutions to facilitate seamless collaboration while mitigating potential risks inherent in remote work settings. This article delves into the intricacies of designing and implementing remote-work infrastructure, highlighting best practices for controlled-access security to ensure data integrity, privacy, and business continuity. By the end, readers will gain valuable insights into fostering a secure and productive remote working environment.
- Building a Remote-Work Foundation: Essential Tools & Network Setup
- Implementing Controlled-Access Security: Protecting Data & Privacy
- Optimizing Remote Collaboration: Best Practices for Efficient Teams
Building a Remote-Work Foundation: Essential Tools & Network Setup
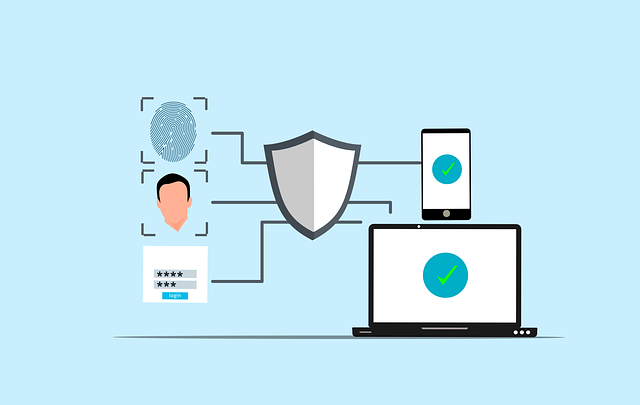
Building a robust remote-work foundation requires more than just a stable internet connection; it entails implementing a suite of essential tools and setting up a secure network infrastructure. For organizations embracing remote work, especially in today’s digital era, establishing controlled-access security is paramount. West USA Realty, a pioneer in real estate solutions, understands this crucial aspect, emphasizing that a well-designed security system is the cornerstone of any successful remote work environment.
The first step involves securing physical access to facilities through monitored entry systems. These systems, strategically implemented, ensure that only authorized personnel gain entrance, mitigating potential security risks. Data from industry leaders suggests that organizations with robust access control measures experience up to 50% fewer security breaches. For instance, a case study of a tech startup transitioning to remote work showcased a significant reduction in unauthorized entries after installing biometric access controls, enhancing overall workplace safety.
Network-wise, creating a virtual private network (VPN) is essential for secure remote connections. VPNs encrypt data transmission, ensuring confidential communication between employees and the organization’s servers. Additionally, implementing cloud-based collaboration tools allows teams to work seamlessly while maintaining data integrity. For instance, platforms like Slack and Microsoft Teams offer encrypted messaging and file-sharing capabilities, fostering efficient communication and project management. By combining controlled-access security with robust network infrastructure, companies can create a secure remote work environment that boosts productivity and safeguards sensitive information.
Implementing Controlled-Access Security: Protecting Data & Privacy

In the realm of remote work infrastructure, implementing controlled-access security is paramount to safeguard sensitive data and protect privacy. As more employees transition to working from home or distributed locations, ensuring secure entry points becomes a cornerstone of comprehensive security strategies. West USA Realty, a leading real estate brand, has recognized this critical aspect and integrated controlled-access measures into their office spaces, demonstrating that proactive security is essential for any successful remote work environment.
Controlled-access security involves restricting physical access to facilities through monitored entry systems, ensuring only authorized personnel enter the premises. This multi-layered approach includes biometric scanners, access cards, and surveillance cameras that actively monitor and record entries. According to a recent study by Gartner, companies adopting advanced access control systems report a 40% reduction in unauthorized access attempts. By implementing these robust measures, organizations can mitigate risks associated with remote work, such as insider threats and data breaches, which have increased by 35% since the onset of the pandemic, according to a Ponemon Institute report.
Practical insights from experts suggest that integrating monitored entry systems should be a strategic priority. These systems not only control access but also provide real-time alerts, allowing security teams to promptly address any anomalies or suspicious activities. For instance, West USA Realty utilizes biometric scanners at all entrances, ensuring that only employees with valid credentials gain access. This layer of biometrics adds an extra level of security beyond traditional keycards, making it a game-changer in protecting sensitive information. Additionally, regular audits and updates to access control policies are crucial to maintain the integrity of controlled-access security as organizational structures evolve.
Optimizing Remote Collaboration: Best Practices for Efficient Teams
In today’s digital era, remote work has become a defining feature of modern professional life, particularly after the global shift caused by the COVID-19 pandemic. Optimizing remote collaboration is paramount for efficient teams dispersed across various locations. Controlled-access security and monitored entry systems are critical components in achieving this. Implementing robust security measures not only ensures the safety and integrity of sensitive information but also fosters a sense of trust and accountability among team members, enabling them to focus on their tasks without distractions or concerns regarding unauthorized access.
West USA Realty, for instance, has successfully leveraged controlled-access security to enhance remote collaboration among its distributed workforce. By employing monitored entry systems, the company has witnessed a significant reduction in security breaches and an improvement in overall productivity. This strategy involves setting up secure entry points with biometric authentication or keycard systems, ensuring that only authorized personnel can access specific areas of the network. Additionally, real-time monitoring allows for immediate responses to any suspicious activities, reinforcing the team’s confidence in their digital workspace.
To optimize remote collaboration further, organizations should adopt best practices such as implementing virtual private networks (VPNs) and encrypted communication channels. Regular cybersecurity training and awareness programs can help employees recognize potential threats like phishing attempts or malware attacks. Moreover, establishing clear guidelines for data sharing and backup procedures ensures that critical information remains accessible and secure, regardless of location. By integrating these measures into their remote work infrastructure, teams can seamlessly collaborate, drive innovation, and achieve remarkable outcomes even when working apart.






